Sunday, July 30, 2006
Mozilla Firefox 1.5.0.5 Portable Edition
read more | digg story
Friday, July 28, 2006
Security Software Vendor BitDefender's Rootkit Detector and Remover
read more | digg story
Zango intentionally using MySpace as a distributor?
read more | digg story
Elaborates Bytes' Virtual CloneDrive
read more | digg story
Find the Name Behind a Malicious IP Address
read more | digg story
Use CableNut to optimize your Internet connection
read more | digg story
Thursday, July 27, 2006
eBay, PayPal Remain Top Phishing Targets
read more | digg story
Digg Labs
Digg is continuing to offer new features. The latest is Stack and Swarm. Both allow users to quickly see what is popular via visual displays.
Wednesday, July 26, 2006
Mozilla Firefox 1.5.0.5 Release Notes
Mozilla has released Firefox 1.5.0.5. This version is predominately security fixes and bug fixes. Even though Firefox 2.0 is schedule to be released soon, Mozilla felt the security vulnerbilities were serious enough to warrant the release of another version of Firefox 1.5x. Please refer to the release notes as to which security vulnerbilities were patched.
BetaNews | Microsoft: IE7 a 'High-Priority' Update
Microsof plans to roll out Internet Explorer 7 before the end of September. Though I am sure Microsoft would love everyone to use IE 7, they have decided to roll out IE 7 as a "high priority" update. Windows users can decide whether to add IE 7 or not. I am not so keen about Microsoft using the Windows Update system to update IE. How many Windows users take the time to read the description for the updates? Oftentimes, users just click away. I think it would be better if Microsoft offered IE through their download site. At least, this way Windows users can make a clear decision to update IE.
Tuesday, July 25, 2006
EasyGoBack - Mouse Gestures for Internet Explorer
read more | digg story
Windows Live Safety Center
read more | digg story
Mozilla Firefox - Have it Your Way!
For all you Firefox fan's out there, here are some extension suggestions which can improve your browsing experience on the Internet. In addition, find tips and tweaks to customize Firefox.
Microsoft releases Windows Live Toolbar
read more | digg story
PopupTest - test your popup blocker software and download software
Any respectable web browser should include a popup blocker. However, not all popup blockers are created equal. PopupTest is a website wherein you can test your web browser's ability to block common forms of popup.
Friday, July 21, 2006
Guide to Useless Services (Windows XP SP2)
Windows XP, by default, starts several Windows services automatically. However, most users don't need these services. By cutting back on the number of services, more resources are available which translates to better performance (i.e. makes Windows faster). This article lists all available services on Windows XP. Read each service's description and decide for yourself if you absolutely need it.
Thursday, July 20, 2006
EFF's Lawsuit Against AT&T is Going Ahead
Well, it appears Electronic Frontier Foundation's (EFF) lawsuit against AT&T is going ahead. The lawsuit was filed against AT&T for its role in aiding the NSA wiretapping Americans without a warrant. The US government petitioned that the lawsuit should be drop because a trial would divulge State's secrets and could compromise the security of the nation. Judge Vaughn, the state judge who is presiding over the case, doesn't think so and has denied the motion to dismiss the lawsuit. Naturally, the federal government is planning to appeal the decision.
CinemaNow launches first secure DVD download and burn service
CinemaNow offers Internet download of DVD movies. They have signed up with several major movie studios. Users can download a movie and play it on their computers. Users can also download movies and burn them on to DVD+/- R and play them on standalone DVD players. Movies are downloaded from the Internet using a secure connection. However, I don't know how they can prevent users from making multiple copies of the movie.
Wednesday, July 19, 2006
Mozilla Firefox Extensions
I am a big fan of the Firefox web browser. Firefox comes with a slew of features which makes surfing the Internet a breeze. And, if these default features aren't enough, you can add more features via extensions. This article from PC Magazine highlights some of the more popular Firefox's extensions.
Tuesday, July 18, 2006
del.icio.us extension for Internet Explorer
Before, the del.icio.us extension was only available for the Firefox web browser. Well, del.icio.us have now made available an extension for IE. Now, adding links to your del.icio.us account is just a few clicks away.
Stealth rootkit makes its debut in the real world
In a computer world of viruses, worms and trojans, rootkits have not gotten a lot of attention - at least until now. What was once only academics, rootkits is now becoming a real threat. They are extremely hard to detect and even harder to remove. BitDefender, F-Secure and Sysinternal have developed rootkit detectors - Sysinternal has recently been acquired by Microsoft. Except to see their rootkit detectors to be added in to their respective Internet Security Suites.
Monday, July 17, 2006
Anonymous Surfing on the Internet
Though there are many commercially available services to hide your identity on the Internet, there are free ones that work just as well.
Today, I will be talking about two of them, Tor and JAP. Tor, believe it or not, was actually developed by the US Navy. However, they abandoned the project some years ago. Luckily, EFF, a not for profit organization, came along and finance the projected. Tor uses a network of “Onion Routers” to hide your identity on the web. Here is how it works, you click to request a website. The request is then routed to the Tor network, where it bounces around randomly before it finally reaches the website. The website can only see the last IP address and not your IP address. Tor’s ability to hide your presence on the Internet is determined by the size of the Onion routers, more routers make it more difficult to discover your really IP address. Tor supports Internet Explorer, Mozilla Firefox and Opera.
JAP is another service that hides your identity on the Internet. It works differently than Tor. JAP uses a static IP address. When you surf to a website, the website sees JAP’s IP address and not yours. I like JAP for a number of reasons. When you use JAP, it displays a meter which shows the level of anonymity. In addition, with Tor, your ISP knows which sites you surf to. This is not the case with JAP, your ISP can not detect which sites you surf to.
Some might say think Tor and JAP are for the paranoids. But, these are uncertain times. In the United States, since 9/11, the NSA has conducted warrant-less wiretapping of Americans. The US government requested information from search engine giants Yahoo!, MSN and Google. Though, I am not sure if “requested” would be the best word. It is more like demanded. Legislation is being drawn requiring ISP’s to keep a record of all customers activities on the Internet.
Movielink to Enable DVD Burning
Downloading movies from the Internet is old news. But, there is talk about downloading movies and being able to burn them on to DVD discs. There are a lot of obstacles to make the latter possible. But, even the possibility is awesome.
Thursday, July 13, 2006
Microsoft Offers Virtual PC for Free
You heard right. Microsoft is making its virtual software, Virtual PC, free for download. Virtual software allows users to run another operating system on top of the installed OS. For example, I have Windows XP installed on my PC. With Virtual PC, I can load and work with Linux OS. It is also a great secrity tool because nothing is installed or saved on the installed OS.
MySpace Takes Steps to Secure User's Safety on Their Site
It is old news about MySpace's problems with safety on their website. MySpace is the largest social network on the Internet, boasting over 90 million users and the most visited site for the month of June 2006. But, as a result of their success, some users have been a arget for pedophiles using the site to find and lure teenager users. MySpace, in response to both local government and parents, have launched a campaign to educated both MySpace's users and parents of the dangers found on the Internet. Unlike previous occasions, in which MySpace's response was lukewarm at best, MySpace has made a generous new effort to safeguard users.
Wednesday, July 12, 2006
Adware pushed on MySpace
Zango, a notorious adware maker, latest target is MySpace. MySpace is the number one social blogsite for teenagers and young adults. Earlier this week, it was discovered that Zango had posted two profiles on MySpace. These two profiles advertising tools to protect MySpace users and another for viewing videos. Today, 180 Solutions, the parent company of Zango, announced that an error was made. 180 Solutions claimed that it had not authorized promotion of its products on MySpace. 180 Solutions promised it would remove these two profiles and any software from the MySpace site.
Tuesday, July 11, 2006
BetaNews | Excel Focus of July Patch Tuesday
Today is "Patch Tuesday" and there are a total of 7 security patches, none of which are highly critical. Several exploits in Microsoft Office's Excel were patched. Other patches fixed vulnerabilities in Windows.
Microsoft puts end to Windows 98 support | CNET News.com
As of today, Microsoft will no longer be supporting Windows 98, Windows 98 SE and Windows Me. Today is the last day that Microsoft will include security fixes for these older version of Windows. Microsoft have been supporting Windows 98 for 8 years, which is the longest period for any Windows version. It is estimated that over 50 million people still use these older version. Those hardest hit by Microsoft's decision to stop supporting these versions are home users, schools and some governmental offices. For these people, Microsoft is promoting inventives to have them upgrade to Windows XP.
Monday, July 10, 2006
Zango Brings Adware to MySpace
180solutions' Zango created profiles on MySpace in order to attract MySpace users in to downloading their adware. Here is how it works. Zango places links on MySpace promising free vidoes. Unexpecting MySpace users click on the link not knowing that by clicking the link they have agreed to allow the installation of adware on their computers. Despite 180solutions pledge to clean up their act, they are at it again.
Firefox Version 2.0 Beta Candidate Released
For all you Firefox lovers, Mozilla is schedule to release the first beta of Firefox 2.0 this Tuesday Jul1, 11th. Firefox 2.0 code name "Bon Echo" will add built-in antiphishing - via Google Safe Browsing extension for Firefox- , automatic spellcheck, an improve manager for extensions and themes to name a few.
A New Danger on the Internet Rootkits
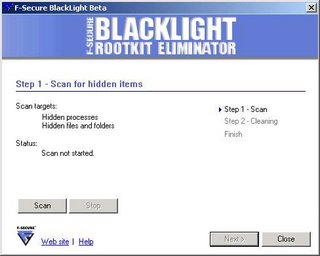 There is a new buzz word on the Internet these days called “rootkit.” Rootkits are a new form of malware. They are difficult to detect and harder to remove. They pose a greater danger than your typical viruses and spyware. What makes them unique is their ability to hide themselves from antivirus and anti-spyware scanners. They accomplish this by hiding in a system’s processes. They are invisible to the task manager. Once installed, they are notoriously difficult to remove (1). Oftentimes, rootkits are used in conjunction with Trojans. Rootkits hides the presence of Trojans, allowing them to record keystrokes, harvest passwords and etc..
There is a new buzz word on the Internet these days called “rootkit.” Rootkits are a new form of malware. They are difficult to detect and harder to remove. They pose a greater danger than your typical viruses and spyware. What makes them unique is their ability to hide themselves from antivirus and anti-spyware scanners. They accomplish this by hiding in a system’s processes. They are invisible to the task manager. Once installed, they are notoriously difficult to remove (1). Oftentimes, rootkits are used in conjunction with Trojans. Rootkits hides the presence of Trojans, allowing them to record keystrokes, harvest passwords and etc..The most notorious of rootkits wasn’t developed by criminals but instead by Sony BMG. Sony distributed several music CDs with their rootkit. The rootkit was part of Sony’s antipiracy campaign. It came to light when a customer, who also happened to be a security software analyst, detected some odd activity on his home computer (2). After thoroughly searching his PC, he found some hidden files. Eventually, it became clear that the hidden files were installed by the music CDs he had played on his PC. What came next was a PR nightmare for Sony. Customers were outrage at Sony’s underhanded campaign to distribute their rootkit. Irrespective of their intent, customers demanded Sony music CDs be removed from the shelves. In addition, Sony was forced to release a patch to remove the rootkit. Unfortunately, the patch was worse than the rootkit. To make matters worse, once it became known that several computers had Sony’s rootkit installed; hackers developed their own malware to exploit the rootkit in order to hide their own malware. Thankfully, security software vendors are developing ways to detect and remove rootkits (3).
Some of the biggest vendors are testing beta versions of their antirootkit scanners, including F-Secure’s Blacklight, BitDefender’s UnCover, Microsoft’s Windows Defender and Sysinternal’s Rootkit Revealer. All these beta versions are available for testing. Important, Windows Defender is available only to Windows user’s that have a genuine license copy of Windows.
1. "Microsoft: Stealth Rootkits Are Bombarding XP SP2 Boxes" – eweek.com
2. "Sony, Rootkits and Digital Rights Management Gone Too Far" -- Mark’s Systinternal Blog
3. "New Rootkit Detectors Help Protect You and Your PC" – pcworld.com
Sunday, July 09, 2006
Human-to-Human Infection by Bird Flu Virus Is Confirmed - New York Times
This the first documented case in which a human was infected by another human, in this case from a son to his father. There have been other incidents where health officials suspected transmission of the virus from one human to another but they were unable to prove it. There is some concern among health officials since human transmission could lead to an epidemic.
What is in Your Computer?
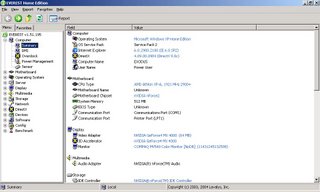
One would think that finding out what hardware and software is installed on a PC is relatively easy, right? Wrong! In regards to hardware, for example, all PC’s have RAM but what kind of RAM. Is it PC3200 or PC2400? How many slots are on the motherbroad and how many of them are free? The PC has a AMD cpu but what kind? Is it a Athlon XP 2800 or Sempron 2800? And, if you think hardware information is difficult to find out, finding out what software a PC has installed is a nightmare. What hotfixes have been installed? Which version of Nero is the PC using? The picture looks very grim for PC owners. However, there are two software programs that can help to shed some light about a PC.
Lavalys’ Everest Home Edition and Belarc Advisor are two freewares that give PC owners everything they need to know about the hardware and software installed. The two freewares offer information about a PC’s hardware and software but, they tend to focus on different areas of a PC. Everest Home Edition provides more information about the hardware in a PC than it does about the software. It displays information about the motherboard, memory, optical drives, storage devices and much more. This information comes in handy if you want to upgrade a piece of hardware. For example, it will tell you how many empty RAM slots are available and what type of RAM is being used. Everest only offers limited benchmarking. Unfortunately, Lavalys’ has stopped the development and support for Everest Home Edition. However, you can still download the software from various computer technology sites, including BetaNews.
Belarc Advisor, on the other hand, focuses on the software installed on a PC. It will display the operating system, installed Windows hotfixes, installed software and their corresponding license keys. Wow, that was a mouth full. This freeware can also be downloaded at BetaNews.
Saturday, July 08, 2006
Privacy on the Internet Temporary Files
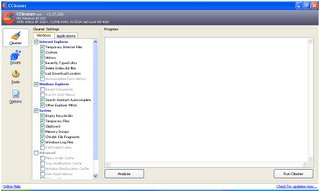
In my previous article, I spoke about cookies stored in web browsers. Today, I will continue my discussion on privacy on the Internet. Deleting cookies is a good place to start but, if you really want to erase your tracks on the Internet, you are going to have to remove more than cookies. Every web browsers records websites visited, search history, download history and temporary Internet files. Those who use a shared computer are especially at risk. Well, thankfully there are many ways to delete these files.
I recommend using a third party utility to remove these files. My recommendation is to use CCleaner (aka Crap Cleaner) I like CCleaner because it supports Internet Explorer, Firefox and Opera. The user interface is clean and very intuitive. Users can select to remove cookies, temporary Internet files, Internet cache and browsing history. It even allows users to select which cookies to keep. CCleaner can securely delete these items by running multiple passes. For instance, you can run 7 passes on the deleted files, which meets Department of Justice standard. Currently, the makers of CCleaner have bundled their software with Yahoo! toolbar to boost revenue. However, you can select to not install the toolbar during installation.
There are other freewares which perform just as well as CCleaner. IE Privacy Keeper is a good alternative; however, it supports Internet Explorer and Firefox. Opera fans won’t be able to use IE Privacy Keeper. But, who knows, as Opera’s popularity is increasing, the guys at UnH Software might want extend support to the web browser. Another alternative is Eusing’s Free Internet Washer; it is a newcomer. Like CCleaner, Free Internet Washer supports IE, Firefox and Opera. The user interface is clean and intuitive. There are a number of settings to fine tune what you want deleted or keep.
In the next article, I will talk about remaining anonymous on the Internet.
AxCrypt File Encryption
Windows Privacy Folder allows PC users to encrypt an entire file folder but is there a encryption utility to encrypt a file? Yes, there is and its name is AxCrypt. AxCrypt is an open-source freeware that adds itself to the contextual menu in Windows. Right click any file and secure it with 128-bit encryption. Jameser walks you through the process step-by-step in plain English and not computer geek language.
Friday, July 07, 2006
Microsoft Adds Privacy Folder To Windows - Security Technology News by TechWeb
Well, Microsoft has released a new free software program for Windows XP Privacy Folder. Windows XP Home Edition does not come with file encryption. Only the pro version provides such a feature. Home Ed. users had to install third party software to get this feature. But, that has change. With Privacy Folder, you can encrypt an entire file folder. It is as simple as drag and drop. In order to download the program, you must have Windows Genuine Advantage (WGA) already installed. The program only works with Windows XP Home Edition w/ SP2.
BitDefender Ships Anti-Rootkit Beta
Computer security vendor BitDefender has launched its first anti-rootkit beta for testing. Rootkits are a new form of malware which disguises its presence on a computer. Oftentimes, other malware is bundled with rootkits. For example, a rootkit can mask a Trojan presence of a computer. BitDefender is the only security vendor working on an anti-rootkit utility. Both F-Secure and Microsoft are developing their own anti-rootkit utility, Blacklight and Windows Defender, respectively. As more and more rootkits are being discovered, security vendors are developing new technology to fight it.
Copy protection hole in Blu-ray and HD DVD movies
Prior to the release of both Blu-ray and HD players, movie studios made it clear that they wanted security measures in place to prevent copying of their high definition copy protected movies. Well, it looks like there is a gaping hole in the security. The exploit involves a basic feature found in Windows' screen capture.
http://www.heise-security.co.uk/news/75103
Thursday, July 06, 2006
Britain Agrees to Extradite Hacker Suspect to U.S.
Britain on Thursday approved the extradition of a computer expert [Gary McKinnon] accused by the United States of perpetrating the world's "biggest military hack of all time." McKinnon is accused of breaking in to several US Government computer systems, including: the US Army, US Navy, the Pentagon and NASA. If convicted, McKinnon could be sentenced to 70 years in prison. After hearing the ruling, McKinnon was quoted as saying he felt let down by the British government.
Wednesday, July 05, 2006
MajorGeeks.com - Download Freeware and Shareware Computer Utilities.
Windows XP comes with several Windows services already activated by default. However, most users don't need many of these services. By decreasing the number of Windows services, it frees up more resources for other tasks. Black Viper has developed a chart to aid PC users in deciding which services can safely be turned off.
Tuesday, July 04, 2006
Ex-Soldier Charged in Rape, Slayings in Iraq
A discharged US soldier, while serving in Iraq, is charged for the murder of 4 Iraqian civilians and raping one of the victim before killing her. Former Private First Class Green and at least four other soliders have been implicated in one of the worst crimes to have been committed by US soliders in Iraq. The FBI and US military have conclude that there is sufficient evidence to continue investigating the alleged crime. Though only Green has been formally charged, three other suspected soldiers have been relieved of from duty.
President George Bush please do everyone a favor and withdraw US soldiers from Iraq. We have no reason to be there. Enough lives have been lost and destroyed for your own private war.
Monday, July 03, 2006
Why Microsoft would want WGA to phone home
Microsoft's WGA aims to deter piracy of Microsoft's popular operating system. But, the company has not been completely forthcoming concerning what WGA actually does. Many users are concerned that Microsoft might have built in a kill switch within WGA. Microsoft has adamantly denied such rumors. Then, there is a problem with WGA Notification. Microsoft does not deny the fact that WGA regularly phones home. Many users are outrage because the company was not upfront with the software. In its zeal to curtail piracy, has Microsoft gone too far with WGA?
Saturday, July 01, 2006
Privacy on the Internet Cookie Control
Internet users should be familiar with cookies, those little bits of information that websites leave on your computer. Cookies can contain various kinds of data. For example, your homepage stores your layout preferences in a cookie. Another example, Amazon.com creates cookies that contain the items you viewed while on their website. And, yet another example, Yahoo! saves your password protected webpages (e.g. Yahoo! Mail.) For the most part, cookies are fairly benign but there are net users who are uncomfortable with them. Some people are uneasy with the idea of having their movements on the net being tracked. It is true that many Internet companies build up profiles of users based on their movements on the net. For example, Google is notorious for using cookies to profile users. Google stores information about what search queries were entered and what links a user clicks on from the result page. It is no secret that Google’s largest source of revenue is ads. The same ads you see on the right side of any result page. Relevant ads that Google determined based on your movements on the net. So, for those who don’t want cookies, how can you delete them? Well, in the following paragraphs, I will touch upon some easy ways to delete the cookies you don’t want, while keeping the cookies you do want.
You can view the cookies stored in Internet Explorer fairly easily. Go to Tools > Internet Options > General tab > [Settings] > [View Files]. You can delete the cookies you don’t want by right clicking on the cookie and selecting delete.
For Firefox, go to Tools > Options > Privacy > Cookies > View Cookies. Delete any cookies you don’t want to keep. In addition, under Cookies, you can choose to selective block or allow certain websites to place cookies; default, this option is turned on. You can also choose to allow cookies from the originating site only. A quick and painless way to delete cookies and temporary internet files is to use the “Clear Private Data” feature, which appears on the same tab.
Much like Firefox, in Opera you can quickly delete cookies and temporary internet file by going to Tools > Clear Private Data. Opera has some very advance cookie management. To access it, go to Tools > Advance > Cookies. Opera allows you to accept all cookies, cookies from the originated site only or don’t accept cookies. Opera also adds cookie control under the contextual menu. On any webpage, right click and scroll down to Edit Site Preferences.