Wednesday, May 31, 2006
BetaNews | Authorities Raid Largest Torrent Site
Well it finally happened, Pirate Bay, the world largest BitTorrent website, has been taken down. In the past, while other BitTorrent website were being taken down, Pirate Bay was able to escape from this purge largely due to lax piracy law in Sweden, where Pirate Bay was located. Equipment was seized and employees were detained. This is a major blow to the BitTorrent community.
Tuesday, May 30, 2006
Exploit Prevention Lab's SocketShield
Figure 1: Socket Shield’s Main Screen
I have been using Exploit Prevention Lab’s SocketShield for close to one month now. SocketShield is one of several new security applications to protect against “zero-day exploits.” Antivirus, anti-Trojan, anti-spyware and other security scanners depend on signatures to detect and remove malware. However, when a new form of malware appears, it takes time for security firms to investigate and prepare an update. It is during this period, computer systems are vulnerable. This is where “zero-day exploit” protection comes in to play. These applications are not dependent on signatures to work. Rather, they look for features common to all malware. You might have heard the term “heuristic protection.” The term is used to describe learning and adapting capabilities. For example, it is common for spammers to misspell words in the subject line in e-mails to circumvent spam filters. Instead of the “f” word they might write “fukk.” This trick works on spam filters but most people will pick up on this misspell. Heuristic capabilities allow software applications to learn and to anticipate these subtle changes.
Socket Shield alerts user when there is a potential threat. The Socket Shield icon sits quietly in the system tray until it detects a threat at which time an alert bubble appears. I haven’t experience any alerts, which means either I surf the Internet safely or the SocketShield doesn’t work. The only real way to find out is to intentionally expose my system to malware, which I am not willing to do. However, for the other features, I can say that SocketShield does what it advertises. SocketShield updates itself automatically with no problems. It monitors my Internet connection’s sockets as advertised.
Exploit Protection Labs was co-founded and run by two veteran Internet security experts, Roger Thompson and Bob Bales. Both of whom worked at PestPatrol, the popular anti-spyware software. Currently, SocketShield is in public beta testing. The testing phase is anticipated to end sometime in June. Afterwards, it will cost $29.95 for a one year subscription.
System Requirements
-
Pentium 1.2 GHz or higher
-
256 MB RAM
-
Microsoft Windows 2000, Windows XP Home and XP Professional
Suggested Reading:
-
Security Startup Targets Unpatched Windows Vulnerabilities –by Robert McMillan, IDG News Service.
-
Anti-Spyware Pros Launch SocketShield Beta –by Jennifer LeClaire
TechNewsWorld.
Windows Process Information - EXE Library
exeLibrary lists the various executable files you might find on your Windows system. It is a good reference if you come across a Windows service you are not familiar with or suspect might be malware. The site also hosts a HijackThis file log analyzer. HijackThis is a popular anti-spyware utility.
BetaNews | Apple Loses Appeal in Trade Secret Case
AppleInsider is a popular website for Apple users. A year ago, the site received information from someone employed at Apple Computers. AppleInsider, in turn, used the information to publish an article on their site. Apple Computers was outraged at the release of company secrets and demanded to know the identity of AppleInsider's source. AppleInsider argued that they are journalist and, therefore, are entitled to protection from revealing their source. The original ruling was against AppleInsider but they applied for an appeal. The ruling of this appeal was for AppleInsider and overturned the original ruling. Read this article for more details.
Monday, May 29, 2006
A Queens Doctor Finds Fighting Hepatitis B Is a Frustrating Task - New York Times
Hepatitis means inflammation of the liver. Hepatitis can be caused by a number of agents, not only pathogens. Hepatitis B is caused by a virus. Infection is caused by one or combination of the three "B's" blood (eg. IV drug use), birth (eg. mother transfer to infant during birth) and "bonk" (sexual intercourse). Anyone can become infected with Hepatitis, most of those infected (80%) recover without any major complications. However, 20% of those infected become chronic carriers - they are unable to clear the virus. Chronic carriers ultimately suffer cirrhosis. A viable liver is essential for life. The liver is responsible for detoxifying the blood.
Sunday, May 28, 2006
Symantec Plugs Anti-virus Worm Hole in Record Time
The title pretty much says it all. Symantec was able to release a patch for the exploit in under 48 hours. Corporate versions of the popular antivirus were vulnerable to the exploit while personal home versions were not vulnerable.
CNN.com - Company: Hackers can crack top antivirus program - May 26, 2006
eEye security firm warns that Symantec antivirus has an exploit that would allow hackers to take over a system. Symantec has neither confirmed or denied the exploit. eEye provided the proof of concept to Symantec and has keep details of the exploit private. Symantec is investigating the alleged exploit. Corporate versions of the software are affected but consumer versons are safe.
Friday, May 26, 2006
Backing Up a DVD-9 to a DVD-5
Yesterday, I wrote about backing up your DVD movies on to a hard drive (HD) as an ISO image. Today, I will be discussing how to back up movies to removable media, CD’s and DVD’s. ISO images are great they are relatively easy to create and use; however, with the average DVD movie being 6 – 9GB in size, it won’t be too long before you use up all your HD space. The most economical alternative is to create a duplicate copy of the DVD movie. Your average single layer DVD blank costs roughly $0.50/disk. But, there is a small problem. You can only record up to 4.7 GB on to a single layer DVD blank (note: these disks are often referred to as DVD-5). That’s a problem since the vast majority of DVD movies have more than 4.7 GB of video (note: these disks are often referred to as DVD-9. One solution is to use a dual layer DVD blank. But, they cost more – usually $1.50 - $2.00/disk – and they take a lot longer to burn. DVD burners can write to a single layer DVD at a maximum speed of 16x speed while writing to dual layer DVD has a maximum speed of 8x. Another solution is to use software to shrink the original DVD movie to fit on to a single layered DVD blank. I will be discussing the latter in this article. In order to accomplish this feat, you will need two software applications. First, you will need software to decrypt and shrink the original video files. Second, you will need software to burn the shrunk video file on to a DVD blank. I recommend using DVD Shrink, for the former, and Nero Express for the latter. DVD Shrink is freeware, but Nero Express is not. However, you can download and use a commercial trial of Nero 7 Ultra Edition; it’s a 30 day trial. Additionally, if you purchase a retail version of an optical drive then it is likely that it came with some burning software –usually Nero or Roxio.
 figure 1: Open Disk in DVD Shrink
figure 1: Open Disk in DVD Shrink
figure2: Backup in DVD Shrink
When all the files are completed, start Nero Express. On the main window, click DVD-Video files (Figure 3). A new window will appear, click on the [Add] icon (Figure 4). A dialog box will appear and you’ll need to navigate to where you saved the shrunk video files. Highlight all the files and press [Add], followed by [Finished] and finally [Next] icon. On the new window, choose the DVD burner you plan to use, set the speed to “maximum” and then press [Burn]. The process may take several minutes depending on the power of your computer and the type of DVD blank you are using.
figure 3: Nero Express copying video files
figure 4: Adding video files to burn
Wired News: Enron's Lay, Skilling Convicted
This is definitely welcomed news that "white collar" crimes will not be tolerated. But, despite the verdicts, employees as well as investors of Enron will not be able to recuperate their losses.
The New Yorker: The Talk of the Town
The controversy surronding the wiretapping by the NSA is still unresolved. Questions concerning the legality and extent of the program are still unanswered. What is pratically alarming is why so many Americans are not concern over the matter.
Thursday, May 25, 2006
BetaNews | MPAA Accused of Hiring a Hacker
This is a new low for Motion Pictures Association of America (MPAA). Torrentspy accuses MPAA of hiring a hacker to obtain company information illegaly.
Wednesday, May 24, 2006
Black Frog takes up Blue Frog spam challenge - vnunet.com
As some of you may know, as of last week, Blue Security has shut down their anti-spam program (i.e. Blue Frog). Unfortunately, one spammer, calling himself "PharmaMaster," launched a DDoS attack on Blue Security which result in their site going offline as well as several other blog sites. But all is not lost. Despite its closing, Blue Frog was very effective. Some proactive people have banded together to launch another Blue Frog-like anti-spam program. But, this time they are taking measures to prevent attacks like the one that closed down Blue Frog.
Backing Up Your DVD Movies on to Your Hard Disk
For the next few posts I will be exploring ways to backup your DVD movies. As for today, I will be illustrating how to backup your DVD movies on to your computer’s hard drive (HD) as an ISO image. In order to do this, you will need to download and install two software programs, both of which are freeware. You will need Lightning UK’s DVD Decrypter and Windows XP Virtual CD Control Panel . Warning, many countries, including the United States, have laws against copying copy protected DVD’s. Users need to be aware of their countries laws regarding copying DVD movies.
In order to install DVD Decrypter, simply click on the installer. Installing Windows XP Virtual CD Control Panel is a little bit more complicated. First, click on the installer. This will install (3) files, including: VCdControlTool.exe, VCdRom.sys and readme.txt. After installing DVD Decrypter, placed the DVD into your optical drive. Right click the optical drive and, under the contextual menu, choose Decrypt using DVD Decrypter.On the main menu toolbar, go to Mode> ISO> Read (figure 1). Next, click on the icon (figure 2) to start decrypting.
Figure1: Setting DVD Decrypter to ISO mode
Figure 2: Start reading of DVD
Now, you are ready to play the ISO image. First, you need to find the (3) files you created earlier from Windows XP Virtual CD Control Panel. By default, the (3) files can be found at C:Document & Settings/
===================
- Windows XP Home or Windows XP Professional
Installation instructions
=========================
1. Copy VCdRom.sys to your %systemroot%\system32\drivers folder.
2. Execute VCdControlTool.exe
3. Click "Driver control" (see figure 3)
4. If the "Install Driver" button is available, click it. Navigate to the %systemroot%\system32\drivers folder, select VCdRom.sys, and click Open.
5. Click "Start"
6. Click OK
7. Click "Add Drive" to add a drive to the drive list. Ensure that the drive added is not a local drive. If it is, continue to click "Add Drive" until an unused drive letter is available.
8. Select an unused drive letter from the drive list and click "Mount".
9. Navigate to the image file, select it, and click "OK". UNC naming conventions should not be used, however mapped network drives should be OK.
You may now use the drive letter as if it were a local CD-ROM device. When you are finished you may unmount, stop, and remove the driver from memory using the driver control.
figure 3: Mounting an ISO image to play
Note: Windows XP Virtual CD Control Panel is not the easiest application to use. There are alternatives applications, such as Daemon Tools or Alcohol 52%
BetaNews | Microsoft: Run Word in 'Safe Mode'
About a week ago, news broke out that a new zero-day exploit had been discovered in Microsoft Word. Microsoft Word 2002 and 2003 are affected. A patch for the flaw is being developed and will be included in the next Patch Tuesday, scheduled for June 13th. For now, Microsoft recommends to open Word in safe mode.
Tuesday, May 23, 2006
Sony rootkit settlement gets final nod | CNET News.com
It appears at least one lawsuit against Sony, who has been accused of including rootkits in their audio CD's, has been resolved. Sony's use of rootkit technology, borne out of their efforts to stop media piracy, was a total fiasco for them. Forget the monetary losses, consumer confidence in the company has plummeted. This is a PR nightmare for Sony.
Monday, May 22, 2006
Ballmer: Symantec suit won't delay Vista | Tech News on ZDNet
Steve Ballmer, Microsoft CEO, told the press today that Symantec lawsuit against Microsoft will not delay the release of Windows Vista. Back in March, Ballmer announced that Vista will not be released until January 2007. Many feared that this latest lawsuit would push back the already overdue new Windows OS.
The Life and Death of Blue Frog Anti-Spam Effort
When I first heard about Blue Frog, I was impressed by their inventiveness to halt spam. Blue Frog was developed by Blue Security, a security firm working out of Israel. Blue Frog had a very innovative way to deal with spammers. First, Blue Security invited e-mail users to join together to create a community, Blue Frog. Each member can add up to 3 e-mail addresses. In addition, members must install a Blue Security software application on to their computers. Second, Blue Security opens several bogus e-mail accounts for each member. These accounts are designed to attract spam – it’s like a honeypot for emails. Whenever a member of the community received spam, Blue Frog would automatically send an opt-out request on behalf of the member. Now, typically, sending one or even a few opt-out request would do very little to discourage a spammer. Spammers send out huge volume of spam; therefore, even if a fraction of the spam got through the spammers still made money. But, what would happen if tens of thousand or even hundreds of thousand sent opt-out request to the spammers? The latter is what Blue Frog does. It uses the power of numbers to stop spam. If spammers attack one member then they had to contend with the other five hundred thousand members. The Controlling the Assault of Non-Solicited Pornography and Marketing Act (CAN-SPAM) law allows a person to send one opt-out request for each e-mail address that received the spam e-mail. It is difficult to say if Blue Frog adhered to the rules as set forth by the law.
Spammers alleged Blue Frog sent out opt-out requests for all of its members, regardless if the member received that particular spam or not. Essentially, spammers accused Blue Frog of launching a DDoS (distributed denial of service) attack. Regardless, Blue Frog was very effective. So effective that spammers took notice. Most spammers were intimidated while others saw this as a declaration of war. One particular spammer, calling himself PharmaMaster, first threatened Blue Frog with releasing the names of its members on to the Web. Blue Security’s CEO, Eran Reshef, didn’t flinched and dismissed it as an empty threat. A week later, PharmaMaster launched an enormous DDoS attack on Blue Security’s website which shut downed their site. To make matters worse, Blue Security redirected their Internet Traffic to their blog. The result of which was to crash thousands of other weblogs. PharmaMaster used a bot army of 10,000+ hijacked computers to launch the DDoS attack.
In response to the attack, Eran Reshef announced that Blue Security will remain vigilant and undeterred by the attack, if only that was true. Within two weeks of the attack, a desponded Eran Reshef announced that Blue Frog will be closing down permanently. This was a serious blow to the anti-spam effort. However, there is talk about forming other Blue Frog service.
Suggested Reading:
PCWorld.com - Spam Slayer: Bringing Spammers to Their Knees – by PC World.
TechWeb | News | Spammer Threatens Anti-Spam Group – by TechWeb.
Wired News: Retaliation for Antispam Success? – by Wired News.
Wired News: Retaliation for Antispam Success? – by Wired News.
In the Fight Against Spam E-Mail, Goliath Wins Again – by Washington Post.
Sunday, May 21, 2006
Blocking Flash Ads in Internet Explorer 6
I hate Flash ads; they take up precious screen space and worse it hogs up bandwidth. Thankfully, there are a number of ways to disable them. For Internet Explorer 6.0, I recommend using Javacool Software’s SpywareBlaster, a freeware. Follow these steps to disable Flash ads using SpywareBlaster.
- Launch SpywareBlaster.
- Go to Tools > Flash Killer.
- Check Disable and Block Flash in Internet Explorer. Viola!
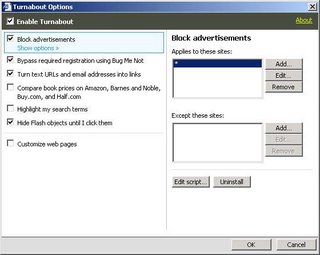
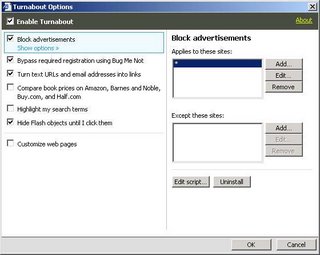
Reify’s Turnabout offers another way to disable Flash ad in IE. Turnabout is freeware and is amazingly easy to use. Turnabout has many other features besides just blocking Flash ads so there is that much more incentive to give it a try. To disable Flash ad using Turnabout follow these simple steps.
- Start Internet Explorer
- Click on the Reify icon which appears on the menu bar.
- Go to Options and check Hide Flash objects until I click them. Viola!
AOL's Active Security Monitor
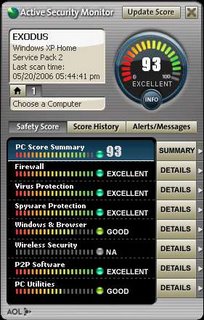
I was surfing the web one day when I came across an article from PC World. The article was on a security tool being developed by AOL. The security tool, called Active Security Monitor (ASM), was designed to scan a computer system and determine the level of security for key areas of the system. These areas include: firewall, virus protection, spyware detection, Windows and browser, wireless security, P2P Software and PC utilities. ASM gives a score for each area and then takes the results and calculates a score for the overall security of the system (max=100 perfect score). In addition, after scanning your system, it will recommend actions in order to increase the security of the system. ASM’s results were not completely accurate. ASM recommended adding a backup utility but I already had one installed. ASM also indicated I had a P2P filesharing when I don’t have any. ASM is still in beta but is free to download and try. For more information, go to AOL’s FAQ webpage.
Friday, May 19, 2006
BetaNews | Critical Word Vulnerability Uncovered
There is a new zero day exploit found in Word documents. The exploit begins with an e-mail which contains a Word document as an attachment. Opening the attachment starts the attack. The exploit is already being used with many attacks reported in China. A patch is being developed by Microsoft and is expected to be released on June 13th, the next scheduled patch Tuesday. Antivirus security firms are already preparing an update for their respective antivirus software. Web users are warned to not open suspicous e-mails.
"F-Secure has dubbed the trojan "Ginwui.A" and says it allows a hacker to: create, read, write, delete and search for files and directories; access and modify the Registry; manipulate services; start and kill processes; and more." --BetaNews.com
Arovax Shield
Thisweek I decided to test out ArovaxShield. Arovax touted its product as a nextgeneration of Internet security. The Shield function is to blockspyware and other malware from installing in the first place. It isnot a new idea; there are a number of intrusion detection softwares(IDS) available. Arovax Shield is freeware. It is totally spywareand adware free. Arovax Shield protect changes in key areas of acomputer systems, including: startup programs, hosts file, InternetExplorer BHO, IE homepage, tracking cookies and certain executablefile associations. The program keeps a log of blocked actions. Itis a very simple program. It does add another layer of protection. However, I recommend BillStudio’s Winpatrol over Arovax Shield. Winpatrol monitors more areas of a system and offers fine granularcontrol of what it monitors.
Technorati Tags security,download
Thursday, May 18, 2006
BetaNews | BellSouth Wants Retraction of NSA Story
Since the USA Today article which accuse AT&T, BellSouth and Verizon of surrendering personal telephone records to the NSA, these telecommunication firms have been busy with damage control. This week, both Verizon and BellSouth released statements denying any illegal release of client information to the NSA. AT&T is being sued by EFF and awaiting trial.
Suggested Reading:
1. NSA has massive database of Americans' phone calls. -- by USA Today.
Wednesday, May 17, 2006
BetaNews | Image Processing Flaw Found in Firefox
A new exploit has been discovered in Firefox 1.5.0.3, the latest stable version. The exploit involves an image tag that can be used to deliver a DDoS attack. Mozilla has not comment on delivering a patch for the exploit.
Wired News: Under Attack, Spam Fighter Folds
It is unfortunate but Blue Security has decided to close its Blue Frog service. Blue Frog was an innovative solution to stop spam. Blue Frog created a community of users - numbering in the hundreds of thousands - that would spend a plethora of opt-out request to known spammers. The program was very successful. Two weeks ago, spammers fought back. One particular spammer, calling himself PharmaMaster, launched a DDoS attack on Blue Security website. The attack shutdown Blue Security's website. When Blue Security redirected Internet traffic to their blog, PharmaMaster launched a DDoS on the blog. As a result of the damage and threat posed by spammers, Blue Security has decided to close Blog Frog. This unfortunately since it sets a precedent. Other spammers could see the success of PharmaMaster's attack as an invitation to copycat.
Tuesday, May 16, 2006
Improve Your Computer's Performance with Acelogix's Tweak N' Tune
There are many software applications to customize Windows XP system. Two popular freewares are Microsoft’s Power Toy’s Tweak UI version 2.10 and Fresh UI. However, I found Acelogix’s Tweak N’ Tune – a freeware as well - to offer the most comprehensive tweaks and it’s easy to use. With this one freeware, you can improve your computer’s performance. Many of the tweaks would otherwise require editing the registry. Should any of the tweaks cause your system to become unstable or unusable – which is highly unlikely – all you need to do undo the change from Tweak N’ Tune. The program keeps a log of the changes you made.
After downloading and installing Tweak N’ Tune (TNT), load the program and click on the Window Tweaks tab on the main page. The program uses a tree diagram to organize the tweaks for easy access.
Explorer Folder:
Folder Customization Cache: set the number of folders to remember to 400. (Default value = 5,000). Less folder customizations frees up memory.
Show AVI Preview in Explorer: uncheck this option to disable AVI preview. For some bizarre reason, when you browse through a file directory containing AVI files (AVI is a video file type), Windows XP automatically loads and runs a preview. I see no good reason to keep this feature.
Thumbnails: by decreasing the size and quality of thumbnails you decrease the time it takes to display thumbnails. Under thumbnail size, decrease the value to 64. Under quality, slide the ruler until it reaches 60. These changes affect new thumbnails. Thumbnails created before this tweak remains unchanged.
File System:
Avoid DLL Caching: for systems with less than 512 MB of memory, check the unload DLL directly. When an application is closed, Windows keeps the DLLs in memory just in case you decide to launch it again. By unloading the DLL directly, you force Windows to free up the memory. For systems with less than 512 MB, Windows can’t spare to keep closed applications in memory because it needs to use it to launch newer applications.
Disk Defragmenter: check off enable boot optimization. The latter allows the boot files to be defragmented along with the system files. The tweak marginally decreases the boot time – every bit helps.
NTFS Options: first, leave enable update of “Last Access” attribute unchecked. After opening and reading a file, Windows places a timestamp on the file when you close the file. This “write action” marginally slows Windows XP. Beware, a small number of backup file applications require the last access attribute to be on. If you experience problems with it turned off then just check the option. Second, uncheck enable 8.3 name creation and allow extended characters in 8.3 file names.
Prefetching: make sure Prefetch both (default) is checked. Prefetching might increase boot time but it speeds up program and file access.
Network
Increase Network Browsing Speed: if you aren’t connected to a network then you can uncheck both options “Printer” and “Schedule Tasks.”
Start Menu and Taskbar
Menu Show Delay: there is a slight delay between clicking on a menu and having it appears. Decrease the delay to have the menu appear quicker. Setting a delay to 0 will display the menu instantly.
Ballon Tips: this tweak doesn’t increase performance but rather takes away an annoyance. Uncheck any ballon tips you don’t want.
Startup and Shutdown
Allow Fast User Switching: if you computer has multiple accounts then you can switch to another account without having to log off the present account. This Windows service is not vital. But, there are situations where this service could help. Disabling this service will decrease the number of Windows services that are loaded. Less Windows services translate to increase speed.
AutoEnd Hung Tasks: occasionally, when trying to shutdown Windows, an application hangs. Windows will then display a dialog box asking permission to force the program to end. Check this option in order For Windows to end the hung program without waiting for a confirmation from the user.
Clear Page File: for security reasons, users may want to clear the page file; however, this significantly delays system shutdown. The page file is the portion of the hard drive which has been converted to act like RAM. When the computer shutdown, the RAM is automatically cleared but the page file is not. This poses a small security concern since some information is retained in the page file.
System
Error Reporting: uncheck allow crash report to be sent to Microsoft. Next, check display a warning when a program crashes.
Memory Settings: if you have 512 MB memory or more then check use large system cache. A large system cache allows Windows to keep as much data in RAM instead of setting it aside for possible future use. Next, check force the core Windows system to be kept in RAM. This tweak forces Windows to use ever bit of available RAM before resorting to virtual memory. Physical RAM is much faster than virtual memory, which resides on the hard drive. When running Windows, the OS converts some space on the hard drive to act like physical RAM (i.e. page file) because Windows needs more memory than the physical RAM can offer. However, virtual memory is much slower relatively to physical RAM. Therefore, keeping information on RAM increases the computer’s performance. Some experts even recommend, for computers with 1 GB of memory or more, to do away with the page file entirely.
Congress may make ISPs snoop on you | CNET News.com
"Wisconsin Rep. F. James Sensenbrenner, the chairman of the House Judiciary Committee, is proposing that ISPs be required to record information about Americans' online activities so that police can more easily "conduct criminal investigations." Executives at companies that fail to comply would be fined and imprisoned for up to one year." -- Declan McCullagh
These are scare times for Americans. Now too long ago, the New York Time released details of NSA wiretapping both domestic and international calls. Now, Congress is drawing up legislation that would encroach on commercial and person privacy on the Internet. Like NSA wiretaps, these new bills are being drawn under the pretense of protecting Americans.
Monday, May 15, 2006
Firefox Extensions
One of the greatest features of Firefox is the long list of extensions. It has been estimated that there are 1,100+ extensions available. So, the problem isn’t a lack of extension but rather deciding which extensions to use. In this article, I have chosen (5) extensions that I have found useful and I think useful for the vast majority of Firefox users.
-
Adblock – the name pretty much says it all. Adblock removes ads found on webpages. I have yet to meet anyone who wants more ads on a webpage. It’s a great tool because fewer ads translate to better readability of the webpage. In addition, rendering webpages is faster because the browser doesn’t need to load the ads.
-
Flashgot – is an extension which integrates several download managers with Firefox. Now, with Flashgot, users don’t have to load the download manager separately. Flashgot automatically fills in the download link(s). Flashgot can download all links on a webpage or only those the user chooses.
-
NoScript – blocks javascripts of any webpage. It is a great security extension because it blocks javascripts from being run automatically. Users can choose to allow a particular script or all of the scripts on a webpage. Users can create a whitelist of webpages that javascript is allowed.
-
Tab Mix Plus – adds even more tab control. The extension can undo closed tabs, duplicate a tab, set shortcut keys and much much more.
-
Fasterfox – this extension optimizes the Internet connection for faster downloading and uploading. This extension is designed for fast connections. It will work for fast DSL and cable broadband connections. The extension will not work for dial-up or slow DSL; there is a good chance that the extension might even slow the connection.
Saturday, May 13, 2006
Optimize Windows XP
You don’t need expensive software programs, like Iolo’s System Mechanic or Norton’s SystemWorks, in order to optimize your computer’s performance. Windows XP comes with several system utilities to clean up and maintain your computer. Follow these (5) easy tasks to get the most out of your system.
Cleanup the clutter that your computer accumulated over time by using Windows’ Disk Cleanup. To access Disk Cleanup go to Start menu> All Programs> Accessories> System Tools> Disk Cleanup. Make sure Temporary files, Download files, Temporary Internet Files and Recycle Bin are checked. Compress old files doesn’t delete any files but, instead, Windows compresses files to free up hard drive (HD) space. If you have plenty of free space on your HD then there is no need to compress these files.
Trim down on the number of startup programs using the “msconfig” command. Go to Start menu> Run> type “msconfig” and [Enter]> Startup tab. Uncheck any program that you don’t need at startup and the click on [Apply]. Caution, do not uncheck your antivirus and firewall programs!
Speed up your computer by defragging your HD. Go to Start menu> All programs> Accessories> System Tools> Disk defragmenter. Click on [Analyze] to see the amount of fragmentation on your HD. Click on [Defragment] to start the process.
Remove any spyware and/or adware by using Microsoft’s Window Defender Beta 2. Download and install Windows Defender. Scan your HD and quarantine any suspect malware. Allow Windows Defender to load on startup in order to monitor your computer and stop any malware that tries to get on to your computer.
Use System Restore to create restore points to undo any harmful changes to your system. Go to Start menu> Help and Support> Undo changes to your computer with System Restore> Create a restore point.
Poll: Most Americans Support NSA's Efforts
Based on a survey conducted by the Washington Post, the majority of Americans approve of the NSA wiretapping telephone calls for the purpose of hindering terrorist activities. In addition, the majority of Americans are willing to sacrifice personal privacy if it would result in better security. My concern is the White House might be inflating the danger of terrorism to legitimize spying on Americans. For example, President Bush pushed for a war with Iraq under the pretense that Iraq had Weapons of Mass Destruction (WMD) and the US needed to act. After extensive investigations, it was determined that Iraq had no such weapons. Could President Bush be doing the same thing with the wiretappings?
Friday, May 12, 2006
Top 10 Windows XP Tips Of All Time | With Vista at least seven months away, we'll all be using Windows XP for some time to come. TechWeb proudly prese
This is definitely a must read for all Windows XP users. The article give tips on how to improve Windows performance.
Obook Plugin for Opera
These days, everyone is talking about Internet Explorer or Firefox and forgotten about other web browsers. The Opera web browser, developed by Opera Inc., is an amazing alternative to Internet Explorer. Unfortunately, since it is not popular, few companies have spent the time developing software for the browser. There is no Yahoo! or Google toolbar for Opera. In addition, there are no extensions like those used in Firefox. However, there are some plugins that are being developed and one really stands out. I am talking about the Obook plugin developed by Dmitry Antonyuk, an Opera enthusiast. People refer to it as the scrapbook extension – found in Firefox - for Opera. I think of it as more like the slogger extension than the scrapbook extension. With the plugin, users can capture the webpage and store it on their hard drives for offline viewing. The Obook plugin supports Opera 8+, including version 9 beta.
Obook allows users to create folders and subfolders in order to categorize the webpages. Currently, Obook is still in beta. Obook 1.0 beta 5 is the most recent release. It still has some bugs but for the most part it is functional. Obook creates a new panel in Opera. The saved webpages appear in the panels. In order to add a webpage, click on the Obook icon. During installation, users can choose to add the icon to the right click context menu, address bar, menu bar, file menu or any combination. Folders are easy to create, just click on the “create new folder” icon which appears in the panel. Users can drag and drop webpages to any folder or subfolder.
Despite its beta flaws, it is a great tool for collecting information from the web and viewing them offline. Two thumbs up for Obook.
Anger grows over NSA surveillance report | CNET News.com
These are uneasy times. In December 2005, the New York Times reported that the National Security Agency (NSA) had been wiretapping telephone lines since 9/11. The purpose of these wiretappings were to investigate possible terrorist threats. However, many disturbing details surfaced. There were no warranties granting permission for NSA to conduct wiretapping. In addition, both international and domestic calls were monitored. Americans were being spied on without any oversight.
Suggested Reading:
1. NSA Monitoring Net Communications --by BetaNews
Thursday, May 11, 2006
BetaNews | NSA Has Record of US-to-US Calls
It is a scare time for American these days. The NSA wiretapping scandal is nothing new but there are a number recent discoveries that the scandal is worse than first thought. President Bush led Americans to believe that only international calls were being wiretapped and not domestic calls. Well, it seems that is not t rue. NSA conducted wiretapping without a warranty without judicial approval and now spying on American civilians. Scary
Suggested Reading:
1. Bush defends NSA data collection program --by USA Today
2. NSA Monitoring Net Communications --by BetaNews
Wednesday, May 10, 2006
Beta Late than Never
Beta Late than Never
Google’s new toolbar beta is only available for IE; they have yet to release a version for Mozilla’s Firefox. Google has added a number of changes and enhancements to their toolbar. The toolbar retains the spellchecker, autolink, autofill and popup blocker. What has been added include customizable “buttons” (more information below), a send to function and enhanced bookmarking.
The days of “one size fits all” are drawing to a close. Personally, I think “buttons” is the greatest addition to the Google toolbar. Prior version did not have this functionality. When you surf to a webpage which contains a search box, right click within the box and choose “Generate Custom Search” from the contextual menu. This will generate a button that you can add to the toolbar. From this button you can run a search as if you entered the term in the original webpage. This feature resembles the “Add a keyword to this Search” function in Firefox. There are already custom buttons that have been developed by third parties and are free to download and install. Google has provided a website for the download of these buttons
The “send to” feature allows the user to send, either the selected portion of a page or the whole page” to their gmail account, Blogger and/or SMS. These features are new to Google’s toolbar but not new to the web. GmailThis is a bookmarklet which automatically loads gmail and launches a “compose new message” window with a link to the current URL address added to the body of the message. Granted, GmailThis only grabs the URL link but you can add the webpage as an attachment. Also, Yahoo! MyWeb 2.0 beta allows users to save cache copies of webpages into their accounts which can then be added as a feed on Yahoo! 360. There are ways to send a webpage via SMS message but they are not as streamlined as the feature seen in the toolbar. Nevertheless, it’s great to have all these features in one place.
The new toolbar has also added a much improved bookmarking feature. Prior to the release of this beta, in order to set bookmarks in Google, you had to go through Google’s Search History. Now, when you find an interesting webpage, you click on the bookmarks icon and select “Bookmark this page…” You can add tags to your bookmarks just like those in Google Search History. And, yes, you can add “stars” to your favorite bookmarks as well.
Tuesday, May 09, 2006
News - IT Security News - SC Magazine UK
A follow-up story to Spammers launching a DDos attack on Blue Security, developers of Blue Frog. Blue Security has recover from the attack. However, there are a number of problems. During the attack, Blue Security diverted their web traffic to their blog. As a consequence of this diversion, both LiveJournal and TypePad came under the DDos attack. There are questions about how Blue Security dealt with the DDos attack. Did they not anticipate by diverting their traffic they would cause the blog host to come under attack? Did they act responsibly?
Sunday, May 07, 2006
Zero Day Protection
It seems like every other week a new zero-day exploit is found. Oftentimes, it is an exploit in Internet Explorer. What makes a zero-day exploit so dangerous is that there is no fix available. Antivirus and anti-spyware scanners rely heavily on virus signatures or definitions to detect malware and remove it. The time it takes for security firms to identify a new bug and develop a fix takes anywhere from hours to days. For example, earlier this year, the WMF exploit found in Internet Explorer took weeks before a patch was released by Microsoft. During the interim, two private security firms released their own patch for the exploit. Their initiative arose from the fear that a patch was desperately needed and the exploit was dangerous enough to not wait for Microsoft’s official patch. This is but one example of why security firms want to develop what they call “zero-day exploit” protection. These applications do not rely solely on updated signatures but rather they scan for features characteristic of malware. These applications are the next generation in security.
Over this past year, several “zero-day” protection applications have been developed. Some of these applications includes: Arovax Shield, Novatix’s Cyberhawk and Exploit Prevention Labs’ Socket Shield. Both Cypberhawk and Socket Shield are still in beta. All three applications are free to download to use. But, Socket Shield is free to use during the one month beta testing. Afterwards, Exploit Prevention Labs will charge an annual fee of 29.95/year. Each company brags that once you install their product, there isn’t any need for antivirus and/or anti-spyware applications. Steve Bass writes in his column, Steve Bass Tips and Tweaks, with Cyberhawk installed you can do away with other security applications. I wouldn’t recommend getting rid of you antivirus and anti-spyware applications just yet. These programs are still a work in progress. Some intrepid people have tried these software programs and many of them encountered problems installing them and/or using them. Read the comments on the Betanews’ website to get a sense of the bugs in these applications.
My recommendation is to wait off from installing these programs. Wait until they work out the bugs. As for now, I recommend using Bill Studio’s Winpatrol, an anti-intrusion application. It is a polished application that has proven itself. Winpatrol 9.8.1.0 is free to download and use. Users can upgrade for a fee to add PLUS features.
Saturday, May 06, 2006
Web Beacons
There many web users who fear that their activity on the Internet is being monitor. Other web users dismiss what they believe to be unwarranted paranoia. But just because they are paranoid doesn’t mean they are not right. This past year, there have been a number of unsettling activities among the search engine giants. In particular, both Yahoo! and MSN have been developing “web beacons.” Web beacons are invisible images and/or cookies designed to trace your steps on the Internet. More alarming, Yahoo! uses web beacons with their free e-mail service. Web beacons reveals if an e-message was received and can also reveal if any action was taken (e.g. the message was read or if the message was forwarded.) Yahoo! isn’t the only company using web beacons. Recently, Microsoft successfully filed a patent with United States Patent and Trademark Office (USPTO). The patent relates to a new technology they have developed to track web activity via invisible cookies (aka Super Cookies).
Cookies aren’t new. But, these web beacons are an entirely different monster. You can view regular cookies from your web browser and delete them just as easily. Unfortunately, that is not the case with web beacons. In order to get rid of web beacons, you need to submit an opt-out request. What troubles me is that I never knew, that by signing up for Yahoo! free e-mail service, I agreed to have them track me via web beacons.
Suggested Reading:
M-Dollar: Microsoft patents the super cookie –by Arstechnica.com
Yahoo web beacons may not shine with users –by About.com
Friday, May 05, 2006
BetaNews | Exchange, Windows Fixes on Tap
Microsoft plans to release 3 patches on May 9th, the next patch Tuesday. Security experts speculate that at least one of these patches will correct a recent exploit found in Internet Explorer which involves IE's object tag.
Thursday, May 04, 2006
Blue Security attack linked to blog crashes - ZDNet UK News
Blue Security developed the Blue Frog anti-spam initative. On Wednesday, May 3rd, Blue Security suffered a denial of service attack. The denial of service attack caused Blue Security website to shutdown. In addition, Blue Security's blog hosted on Six Apart also caused the shutdown of Typepad and LiveJournal.
"American Express"
A new scam which involves the American Express Card website has been discovered. This scam distinguishes itself from other scams because the website is genuine. Yes, it is the real American Express website and it is using a secure line. What is not genuine is the popup window which appears on the website. The popup window asks for the user Social Security number, Mother's maiden name and date of birth. The scam is a result of a Trojan that infects a user's computer. Once infested, the Trojan waits for the user to get online and surf to the American Express website. Once there, the Trojan displays the fake popup window. Please read the article for more details.
Suggested Reading:
1. American Express Beware of Phony Log-in Screen --byRyan Naraine, eWeek.
Wednesday, May 03, 2006
Iron Mountain loses backup tapes again - ZDNet UK News
How does Iron Mountain, a data protection and storage firm, stay in business? Please read this article about blunders that lead to identity theft.
Firefox Memory Leak Problems
Thereis no question that Mozilla’s Firefox is an excellent webbrowser free of bloatware. Firefox growing popularity is whatmotivated Microsoft to update their defunct Internet Explorer. Unfortunately, Firefox’s users almost uniformly complain aboutFirefox’s memory leaks. Firefox memory consumption oftentimesexceeds 100,000 KB which is intolerable. So, the question is what iscausing the memory leaks and, more importantly, how to rectify theproblem. Many “how to” articles have been written toshed some light on the problem and offer remedies as well.
Memory leaks due to troublesome Firefox extensions. Many experts believe that the memory leak is not inherent in the web browser but instead due to certain extensions. Suggested Reading: Reducing Your Memory Usage in Firefox –by CyperNet.com.
Memory leaks due to the back cache feature. Starting with version 1.5, Firefox included a fast back navigational feature which allows for quick rendering of previously loaded webpages. More saved back webpages resulted in more memory usage. Suggested Reading: About the Firefox “memory leak.” –by weblogs.mozillazine.org.
Memory leaks due to relegating too much memory to the cache memory. Suggested Reading: Firefox Tweaks, Extensions and Optimizations. –by Golomer.com
Memory leaks in older versions of Firefox. Firefox 1.5.0 was riddled with memory leaks. Firefox 1.5.0.2 included many memory leak fixes. Suggested Reading: Did Mozilla Really Fix the Memory Leaks with Firefox 1.5.0.2 –by CyperNet.com.
Technorati Tags firefox,browser,howto
TechWeb | News | Spammer Threatens Anti-Spam Group
Blue Frog is an open source project designed for the purpose of stopping the spread of spam e-mails. The idea behind Blug Frog is building a community of e-mail users who act in concert to discourage spammers from sending more spam. For example, when members of the community receives spam, Blue Frog automatically traces the origin of the spam. Once found, Blue Frog then fills out opt-out forms requesting the spammer to stop sending spam to their members. Alternatively, if no opt-out form is available, Blue Frog would then fill out complain forms. Blue Frog has been very effective at stopping spam for its community. It is because of its success that a spam king is threaten to release the e-mail addresses of Blue Frog's community in an effort to deter its [Blue Frog] use. Blue Frog's chief executive, Eran Reshef, states that this is a hollow threat since their database of users are encrypted and can not be accessed by spammers. Read the article for more details.
Suggested Reading:
1. Blue Frogs, Spam and Email --by John Stith, webpronews.com
Tuesday, May 02, 2006
Determine Your Connection Speed
Whetheryou’re using cable, dsl or dial-up, Speakeasy’s SpeedTest can determine your download and upload connection speed. Speakeasy works for both Internet Explorer and Firefox. In order touse Speakeasy, you will need Macromedia Flash Player 8.0+. If youare using Firefox then be sure to disable Flashblock, NoScript andAdblock or enter Speakeasy’s URL into the allow lists. The testwill take a minute or two depending on the connection type you use. Once started, do not touch anything (e.g. no mouse clicking or typingor changing tabs). Speakeasy will first calculate your downloadtime. Wait few seconds and the upload speed will be calculated. Important, it is rare to have the same speed for both download andupload. Usually, the download speed is greater than the uploadspeed. Speakeasy uses several servers that span the globe. You canuse the server closest to you or you could experiment and try all ofthem. Enjoy.
FileForum | Mozilla Firefox for Windows
To all your Firefox users, Firefox 1.5.0.3 has been released. The new version contains a bug fix for an exploit found in version 1.5.0.2. The exploit has been labeled "not critical" by Secunia, a security firm. However, Mozilla felt it necessary to release a bug fix. At the very worst, the exploit could cause a denial of service attack.
Monday, May 01, 2006
Stopdesign | Google Calendar tips
Google Calendar is a new player in the online calendar game. Stopdesign was kind enough to lists several tips and tweak so that you can get the most out of Google Calendar.